Send Data to Azure Cloud in the Key-Value Format
About this task
- The iFIX collector
- The MQTT collector
- The ODBC collector
- The OPC Classic DA collector
- The OPC Classic HDA collector
- The OPC UA DA collector
- The OSI PI collector
- The Server-to-Server collector
- The Simulation collector
- The Windows Performance collector
- The Wonderware collector
{"body":[{"tagname":"Azure_Iot_simulation_tag_1","epochtime":1629730936000,"tagvalue":7129.124023438,"quality":3},
{"tagname":"Azure_Iot_simulation_tag_2","epochtime":1629730936000,"tagvalue":123.3738924567,"quality":3}]
,"messageId":436 ,"statusCode":0}You can also send data in the KairosDB format.
Procedure
-
Create Azure IoT Hub.
Tip: To choose the correct Azure IoT Hub tier based on your data throughput, refer to https://docs.microsoft.com/en-us/azure/iot-hub/iot-hub-devguide-quotas-throttling. For guidance on choosing the appropriate subscription, refer to https://azure.microsoft.com/en-us/pricing/details/iot-hub/
-
After you create Azure IoT Hub, select Go to resource,
and then note down the hostname:
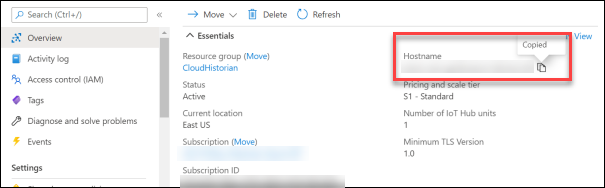
-
Create devices in Azure IoT Hub to group related tag information; thus mapping a collector
instance to a device. We recommend that you create one device per collector
instance. Ensure that the device is running.
When you create a device, use the following guidelines to choose the authentication type:
- Symmetric Key: Select this option if you want to use a Shared Access Signature (SAS) authentication.
- X.509 Self-Signed: Select this option if you want to create self-signed certificates using OpenSSL. We recommend that you use these certificates only for testing purposes. For instructions, refer to https://docs.microsoft.com/en-us/azure/iot-hub/tutorial-x509-self-sign.
- X.509 CA Signed: Select this option if you want to use CA-signed certificates
-
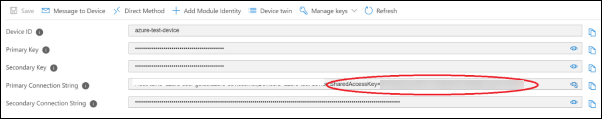
If you have selected Symmetric Key in the previous step,
select the link in the Device ID column, and note down the
shared access key value.
- Access Configuration Hub.
-
In the NAVIGATION section, select
Collectors.
A list of collectors in the default system appears.
- If needed, select the system in which you want to add a collector instance.
-
If needed, select the system in which you want to add a collector
instance.
-
In the upper-right corner of the main section, select
 .
.
The Add Collector Instance: <system name> window appears, displaying the Collector Selection section. The MACHINE NAME field contains a list of machines on which you have installed collectors. -
In the COLLECTOR TYPE field, select a collector type,
and then select Get Details.
The INSTALLATION DRIVE and DATA DIRECTORY fields are disabled and populated.
-
Select Next.
The Source Configuration section appears.
- As needed, enter values in the available fields.
-
Select Next.
The Destination Configuration section appears.
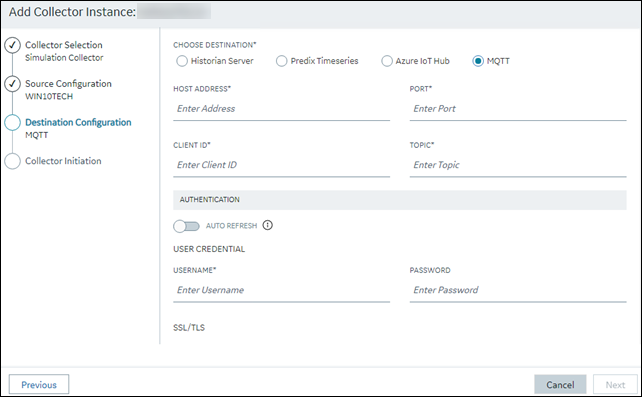
-
Select MQTT, and provide values as described in the
following table.
Field Description HOST ADDRESS Enter the host name of the resource that you have noted down in step 2. A value is required and must be in the following format: <Azure IoT Hub name>.azure-devices.netPORT Enter 8883. CLIENT ID Enter the ID of the device that you created in step 3. A value is required and must be unique for an MQTT broker. TOPIC Enter devices/<device ID>/messages/events. AUTO REFRESH Indicates whether you want to automatically create/refresh the SAS authentication token when it expires. - If you switch the toggle off, you must manually provide the token as soon as it expires.
- If you switch the toggle on, you must provide the shared access key that you have noted down in step 4. And, you can leave the PASSWORD field blank.
USERNAME Enter a value in the following format: <host name or IP address>/<device ID>/?api-version=2018-06-30PASSWORD Enter the SAS token. This is applicable only if you have selected Symmetric Key in step 3 and if you have switched off the AUTO REFRESH toggle. For instructions on generating a SAS token, refer to https://docs.microsoft.com/en-us/azure/cognitive-services/translator/document-translation/create-sas-tokens?tabs=Containers.
DEVICE SHARED KEY Enter the shared access key value that you noted down in step 4. A value is required. This is applicable only if you have selected Symmetric Key in step 3 and if you have switched the AUTO REFRESH toggle on. CA SERVER ROOT FILE Enter the path of the CA server root file that you want to use. You can find the file here: https://github.com/Azure-Samples/IoTMQTTSample/blob/master/IoTHubRootCA_Baltimore.pem. CLIENT CERTIFICATE Enter the path to the client certificate. A value is required. This is applicable only if you have selected one of these options in step 3: - X.509 Self-Signed: If you have selected this option, you can generate the certificate using OpenSSL.
- X.509 CA Signed: If you have selected this option, you would receive the certificate from CA.
PRIVATE KEY FILE Enter the complete path to the private key file. A value is required. This is applicable only if you have selected one of these options in step 3: - X.509 Self-Signed: If you have selected this option, you can generate the key file using OpenSSL.
- X.509 CA Signed: If you have selected this option, you would receive the key file from CA.
PUBLIC KEY FILE Enter the path to the public key file. This is applicable only if you have selected one of these options in step 3: - X.509 Self-Signed: If you have selected this option, you can generate the key file using OpenSSL.
- X.509 CA Signed: If you have selected this option, you would receive the key file from CA.
CHOOSE CONFIGURATION The type of the configuration to specify the tags whose data you want to collect. Select one of the following options: - Historian Configuration: Select this option if you want to add the tags manually. If you select this option, the CONFIGURATION HISTORIAN SERVER field appears.
- Offline Configuration: Select this option if you want to provide the tag names using the offline configuration file instead of adding tags manually. By default, this file is located in the following location: <installation folder of Historian>\GE Digital\<collector name>
CONFIGURATION HISTORIAN SERVER The host name of the machine from which you want to access Historian Administrator to add the tags manually for the collector. This field appears only if you have selected Historian Configuration in the CHOOSE CONFIGURATION field. -
Select Next.
The Collector Initiation section appears.
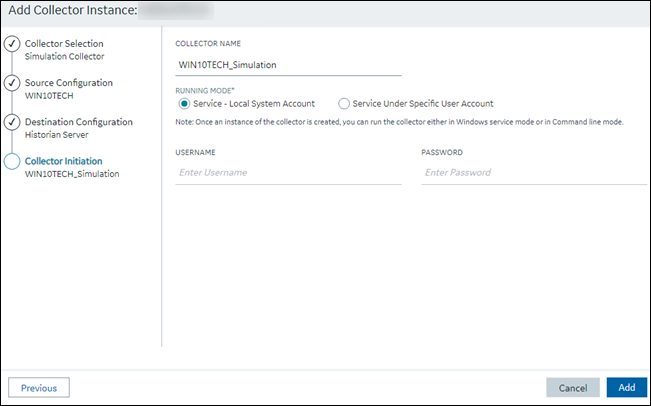
- Enter a unique collector name.
-
In the RUNNING MODE field, select one of the following
options.
- Service - Local System Account: Select this option if you want to run the collector as a Windows service using the credentials of the local user (that is, the currently logged-in user). If you select this option, the USERNAME and PASSWORD fields are disabled.
- Service Under Specific User Account: Select this
option if you want to run the collector as a Windows service using a
specific user account. If you select this option, you must enter values
in the USERNAME and
PASSWORD fields. If you have enabled the
Enforce Strict Collector Authentication
option in Historian Administrator, you must provide the credentials of a user who is added to at least
one of the following security groups:
- iH Security Admins
- iH Collector Admins
- iH Tag Admins
If you choose the first option, you can also configure the collector to start automatically when you start the computer, or, in the case of iFIX collectors, whenever you start iFIX.
-
Select Add.
The collector instance is created.
-
Specify the tags for which you want to collect data.
- If you have selected Historian Configuration in the CHOOSE CONFIGURATION field, specify the tags manually.
- If you have selected Offline Configuration in the CHOOSE CONFIGURATION field, specify the tags using the offline configuration file.
The collector begins sending Historian data to the Azure IoT Hub device that you have created.