Map LDAP Groups With Proficy Authentication
About this task
If you want LDAP users to use Proficy Authentication, you must map the corresponding LDAP groups with UAA group created during the Proficy product installation.
Procedure
-
From your desktop, launch the Proficy Authentication application.
The shortcut icon on your desktop is created after you install Proficy Authentication.
-
Select the Identity Providers tab.
The UAA/LDAP/SAML Connectivity Tool appears.
- Select the Map Existing LDAP Groups check box.
- In the UAA Connection section, provide values as specified in the following table.Important: The values that you provide in this step must match the values that you provided while installing your Proficy product. These values are required to connect to Proficy Authentication. Proficy Authentication works only with a single instance of UAA, which is specified during Proficy Authentication installation. After installation, you cannot change the instance of UAA that Proficy Authentication will use.
Field Description URL This information is read-only. The authorization server URL of the Proficy Authentication server is populated by default. This is the UAA Base URL that you specified during installation . Client ID Enter the client ID of the Proficy Authentication server that you specified for Admin Client ID during installation. Client Secret Enter the client secret configured for the OAuth client that you specified for Admin Client Secret during installation. - Select Test.If connection to the Proficy Authentication server is established, a message appears, confirming the same.Note: Currently, the Test button displays a successful connection for LDAP even when no security certificate, or a bad certificate is found.
- In the LDAP Connection section, provide values as specified in the following table.
Field Description URL Enter the base URL of the LDAP server (for example, https://localhost). Bind User DN Enter the distinguished name of the bind user (for example, cn=admin, ou=Users, dc=test, dc=com). Password Enter the password for the LDAP user ID that searches the LDAP tree for user information. Skip SSL Verification (UAA restart required) Select this check box if you do not have the certificate to access the LDAP server. Messages are still encrypted, but the certificate is not verified for correctness. Do not select this option if you are not confident of the direct connection to the LDAP server; it could result in redirected traffic outside of your controlled network.
User Search Filter Enter the subdirectories to include in the search (for example, cn={0}). User Search Base Enter the starting point for the LDAP user search in the directory tree (for example, dc=developers,dc=com). Group Search Base Enter the starting point for the LDAP group search in the directory tree (for example, ou=scopes, dc=developers, dc=com). Max Group Search Depth Enter a value to define the maximum depth for searching LDAP groups. (This may impact performance for very large systems.) By default this value is 10. Group Search Filter Enter the subdirectories to include in the search (for example, member={0}). 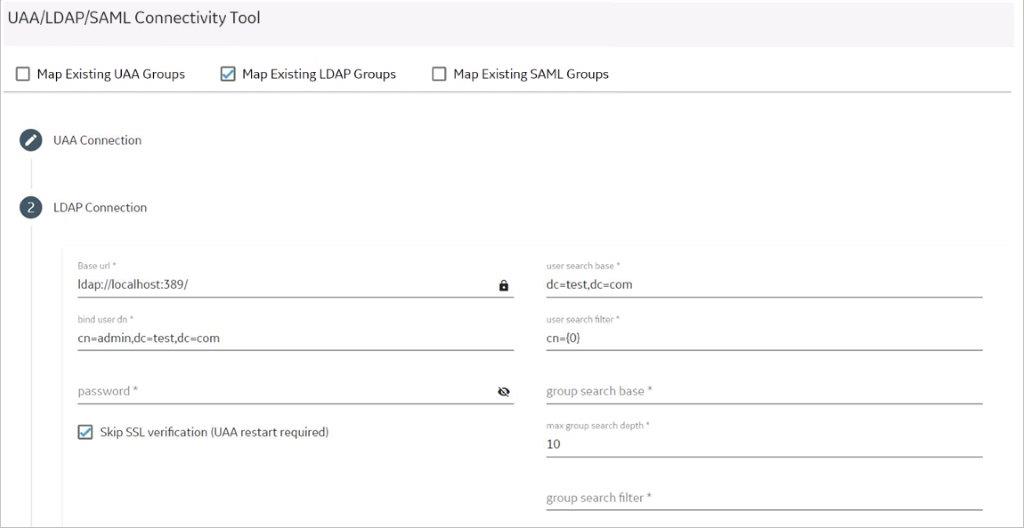
- Select Test, and then select Submit.If connection to the LDAP server is established, a message appears, confirming the same.
- Select Test again, and then select Continue.In the LDAP Mapping section, the drop-down list box contains a list of groups in Proficy Authentication.
-
In the drop-down list box, select the Proficy Authentication group to which you
want to map LDAP groups. You can also search for a group in the LDAP
Groups Search Filter box. When searching, be sure to use the
standard LDAP query language for your search.
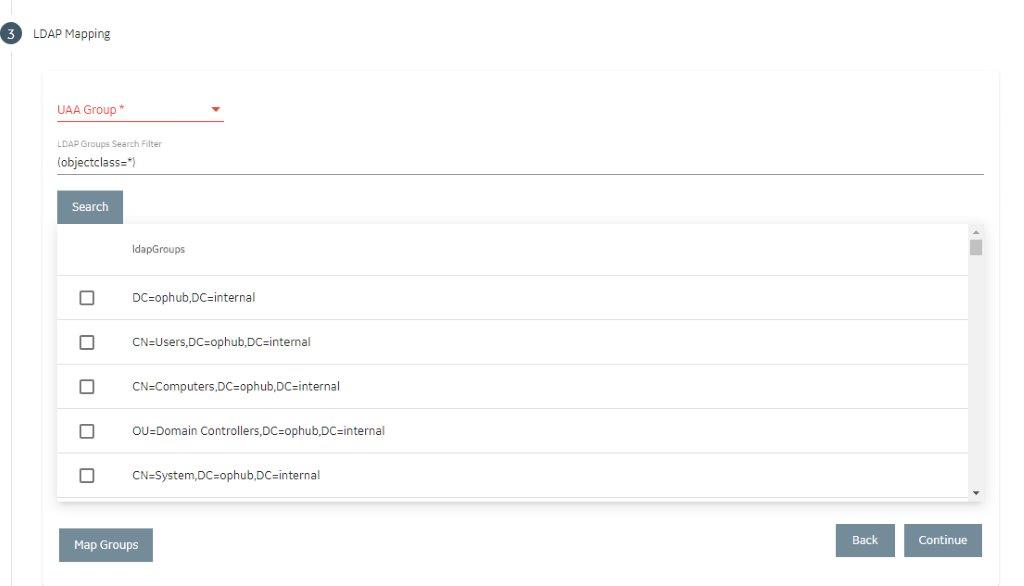 Note: If a group is already mapped to the Proficy Authentication group that you have selected, the check box is already selected.
Note: If a group is already mapped to the Proficy Authentication group that you have selected, the check box is already selected. - Select Map Groups.A message appears, confirming that the LDAP groups are mapped to the Proficy Authentication group.
- Repeat steps 8-10 for all the Proficy Authentication groups that you want to map.