Enable Windows Auto-login in an Active Directory Environment
This topic describes how to enable Windows Auto-login in an Active Directory Environment.
About this task
Note: Windows Auto-login authentication is not supported on a local client browser if
Proficy Authentication is installed on the same machine.
Procedure
-
Install Proficy Authentication.
During installation (standalone or as part of Operations Hub), use a FQDN that has a proper record on the DNS server as the primary host name. A local name will not work. IP address is not recommended either.
-
Log in to Proficy Authentication, and configure LDAP identity provider using the
domain’s LDAP server.
Test the LDAP login to make sure it works for LDAP users.
-
Create a user account on the Active Directory domain.
Proficy Authentication (UAA) uses this account for validating Windows domain credential (Kerberos service tickets) presented by browser on user’s behalf.
-
Build the Service Principal Name (SPN).
The SPN is formed based on the host’s canonical domain name, not any other aliases. It is in the form of
HTTP/fqdn@REALM, where HTTP is literal. The fqdn should be replaced by the actual FQDN of the host, typically in lower case, and REALM be replaced by the Active Directory domain name, typically in upper case.For example, if the Active Directory domain name istest.net, the host’s FQDN isuaa.test.net, then the full SPN isHTTP/[email protected] -
Create a keytab file for this account.
The keytab file contains the cryptographic keys that are private to this account. Each key is specific to an encryption algorithm, so all the algorithms allowed for the account must be accounted for in the keytab file. It is recommended to specify
Allfor the crypto parameterCrypto. The following is an example of howktpass.execommand is used to generate a keytab file on a domain server:ktpass.exe -out xyz.keytab -mapUser [email protected] +rndPass -mapOp set +DumpSalt -crypto All -ptype KRB5_NT_PRINCIPAL -princ HTTP/[email protected] -
Copy the generated keytab file to the machine where Proficy Authentication is
installed.
For convenience, it is recommended to place the keytab file under the same directory as
uaa.ymlfile, which is found in either of these locations:C:\ProgramData\GE\Operations Hub\uaa-configC:\ProgramData\GE\Proficy Authentication\uaa-config
The keytab file contains crypto information, So it is strongly recommended to set a security for the file. The file should not be readable by non-privileged user accounts, except for the service accountNT SERVICE\uaaTomcat. -
Configure UAA with the SPN and keytab file.
-
On client machines, make sure that the Proficy Authentication host is recognized on
the Local Intranet zone or as a Trusted Site.
If not recognized, the Chrome browser will not request a Kerberos ticket to send to Proficy Authentication. For test/staging purposes, it can be done via Control Panel as shown here:
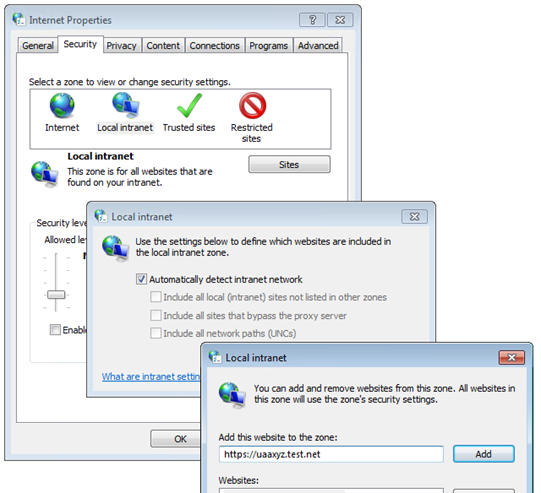 If the setting is configured interactively using Control Panel, then it is effective only for one user on one client machine. To configure for all users on one client machine, use local group policy. In an enterprise setting, an administrator should configure client machines via group policy. You can access the policy from , as shown here:
If the setting is configured interactively using Control Panel, then it is effective only for one user on one client machine. To configure for all users on one client machine, use local group policy. In an enterprise setting, an administrator should configure client machines via group policy. You can access the policy from , as shown here: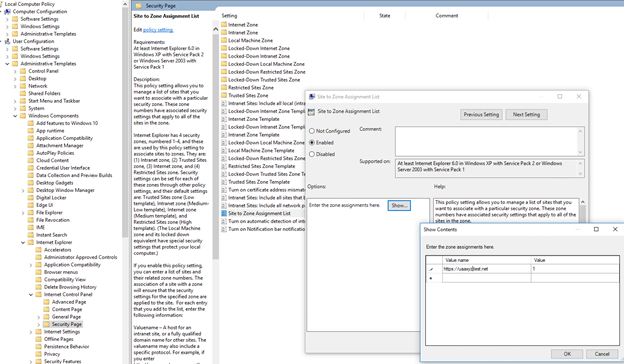
- If Operations Hub is installed on a different machine than Proficy Authentication (i.e., in case of External Proficy Authentication or External UAA), then only the external UAA host name matters.
-
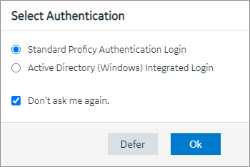
As an administrator, you may allow users to interactively choose an authentication
option, or you may set it in the URLs you distribute to users.
Note:
- It is not necessary for Proficy Authentication (or Operations Hub if different) host to be a domain member; it only needs to have a valid DNS record. However, both the user and the client machine that the user has logged into must be of a domain user/domain member respectively, in order to produce a Kerberos ticket to authenticate with Proficy Authentication.
- For Administrator’s Console, the only way to use Windows Auto-login is to
use the additional query parameter in the URL:
https://xyz.test.net/site/adminconsole?authOption=kerberos