Configure Internet Protocol Security (IPSEC)
About this task
Procedure
-
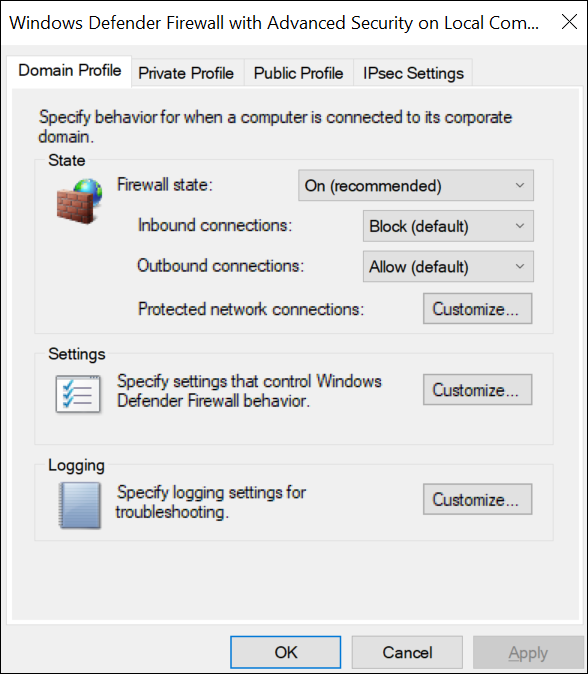
Run
wf.msc.The Windows Defender Firewall with Advanced Security window appears. -
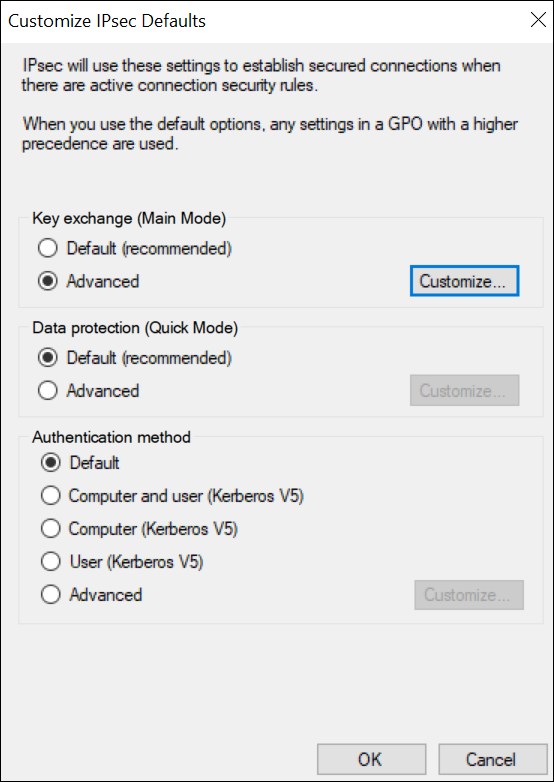
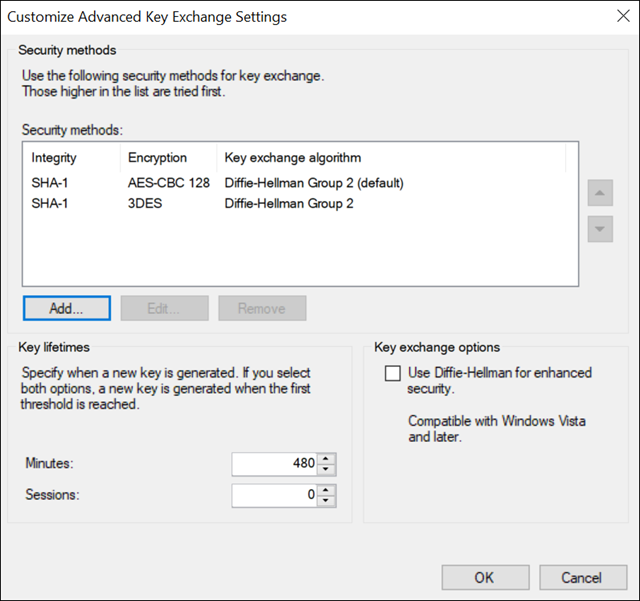
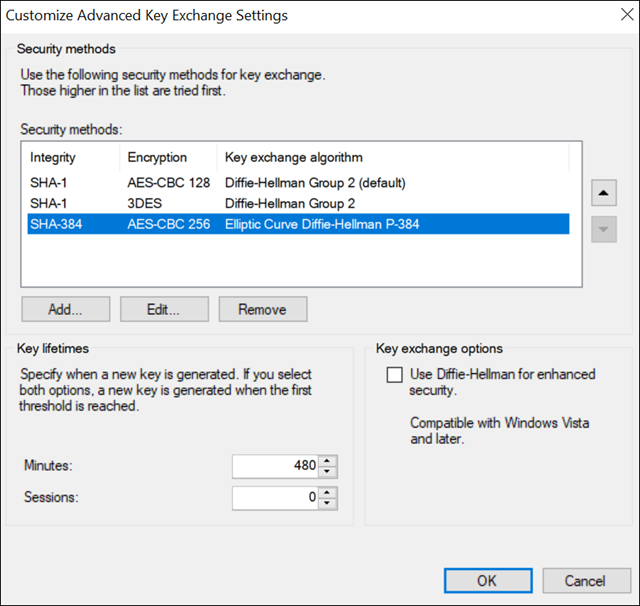
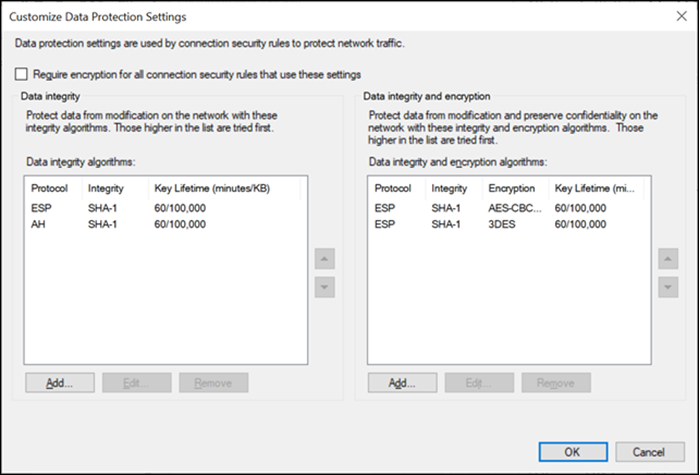
Create a security method:
-
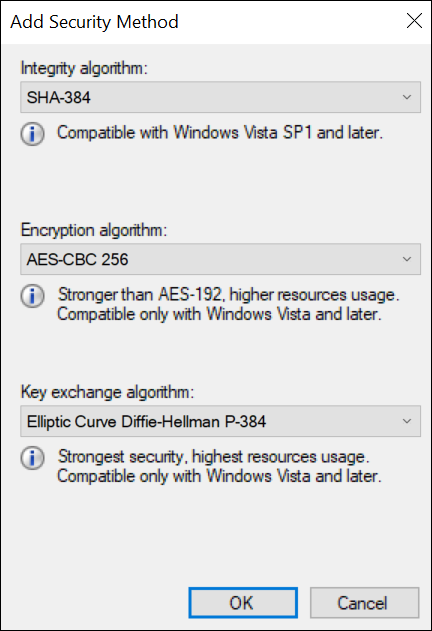
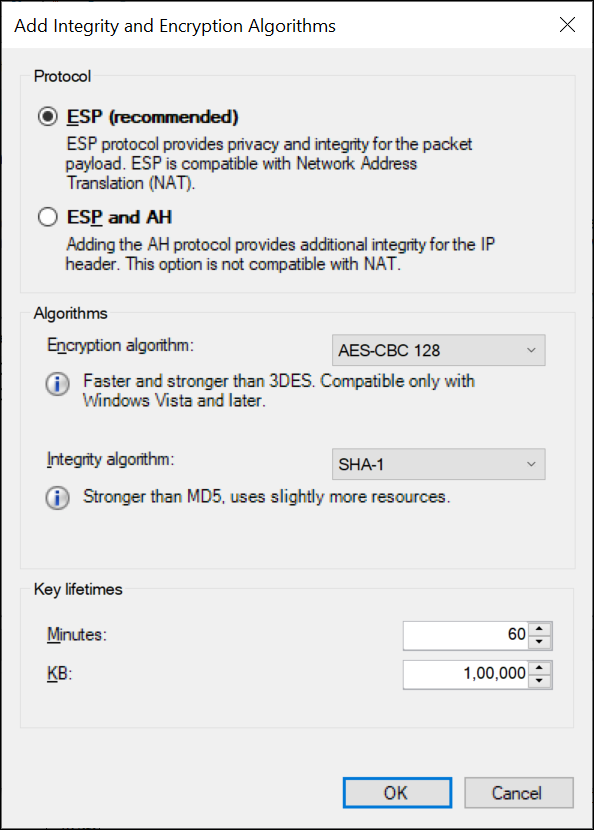
Add integrity and encryption algorithms:
-
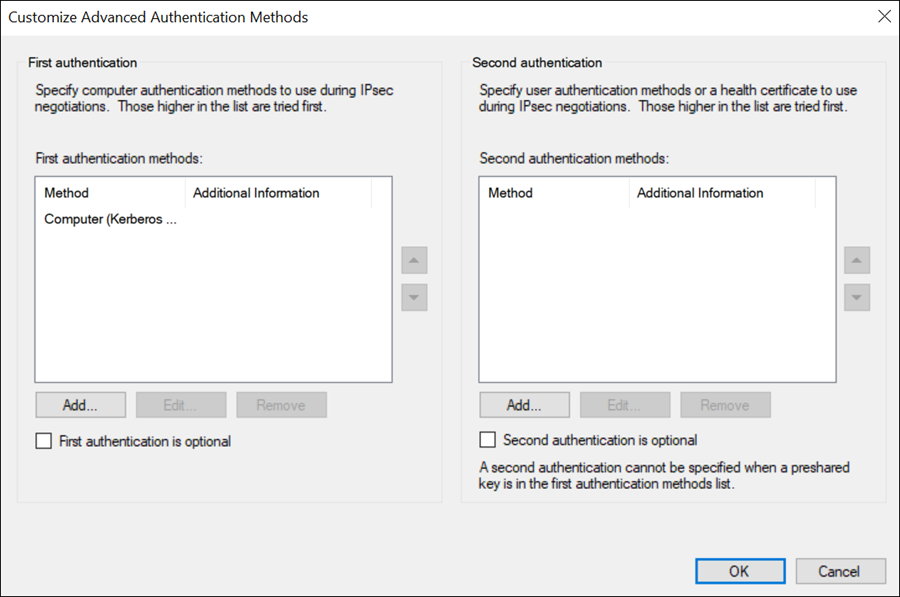
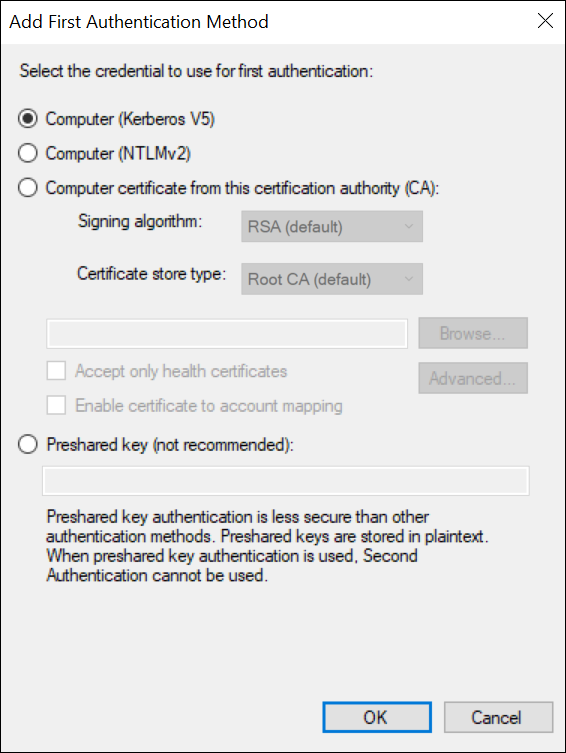
Create a first authentication method:
-
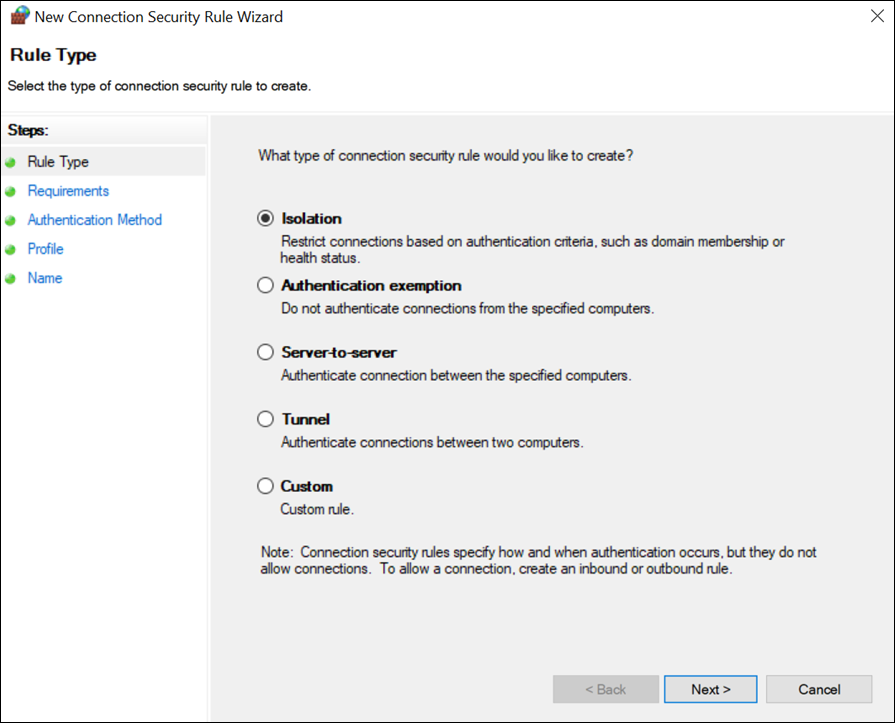
Create a connection security rule:
For Windows x86, run the following set of commands to create a rule:
For other versions, perform the following steps:netsh advfirewall consec add rule name=""<rule name>"" endpoint1=any endpoint2=any protocol=tcp port1=any port2=2010 action=requestinrequestout -
If using Microsoft Windows Server 2019, 2016, 2012 R2 and/or Windows 8, 8.1,
open up port number 5000:
IPSEC is now configured on the machine.
- Repeat all the steps above on all the machines that host the Historian server and/or its components/clients.
-
To verify that the IPSEC cryptography is used: