Configure Azure AD as SAML IDP
This topic describes SAML configuration with Azure AD (Active Directory).
Before you begin
- Visit https://azure.microsoft.com/en-us/free/ and create an account.
- Add an enterprise application. For more information, refer to Microsoft Azure documentation.
Ops Hub Devis the example enterprise application used in the procedural steps (refer to the figure in step 2). - Create at least one user and group.
About this task
- Creating a SAML app in Azure (steps 1-5).
- Configuring Azure metadata xml in Proficy Authentication (steps 6-7).
Procedure
-
Download Proficy Authentication
saml-sp.xmlmetadata file. Refer to Enable SAML on how to download the file. -
Sign in to the Azure portal, and upload
saml-sp.xml.- From left menu, select .
- Select Upload metadata file.
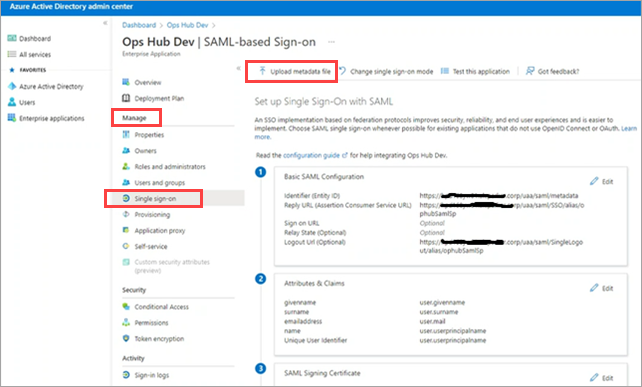
-
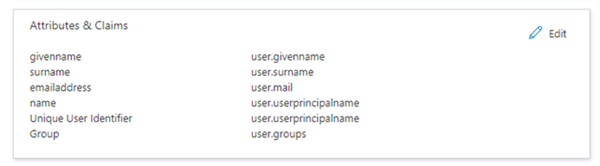
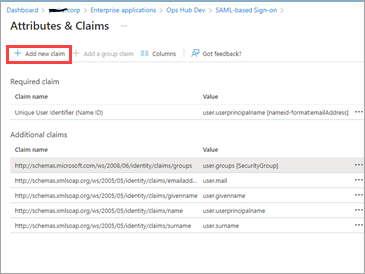
Perform user and group attribute mapping in Azure.
-
Under the SAML Signing Certificate section, download the
Federation Metadata XML file.
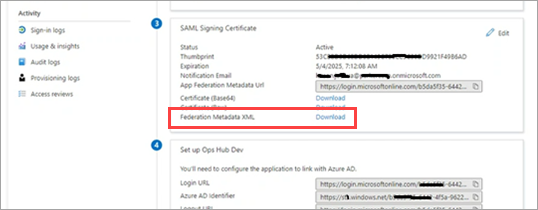
-
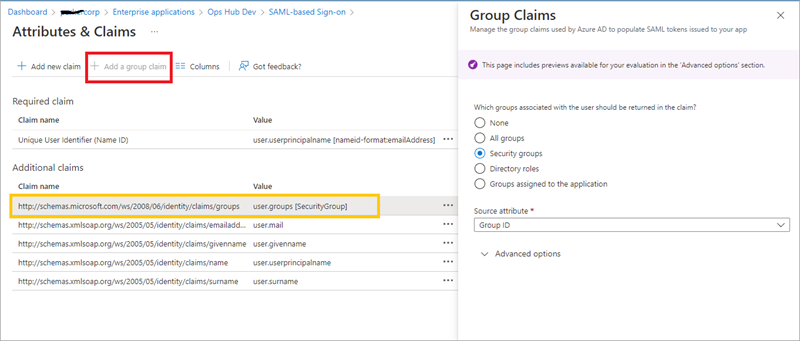
Perform user group mapping in Azure.
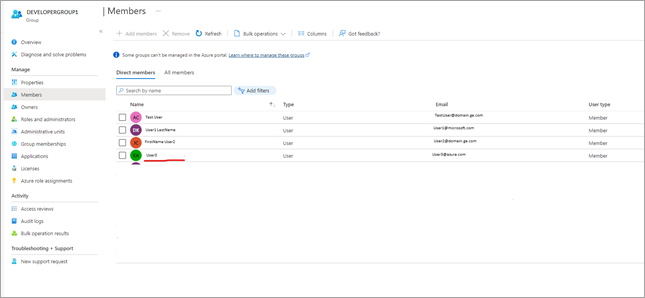
-
Log in to Proficy Authentication and do the following:
-
To test SAML authentication, visit Operations Hub login page, and select
Sign In With Azure.

- You should login successfully. In Azure portal, you can access the logs to
verify successful logins:
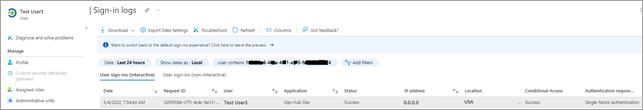
- If login access is denied, then verify the group attribute name and group name from SAML Azure (see troubleshooting below). Clear the cache and login again.
- You should login successfully. In Azure portal, you can access the logs to
verify successful logins:
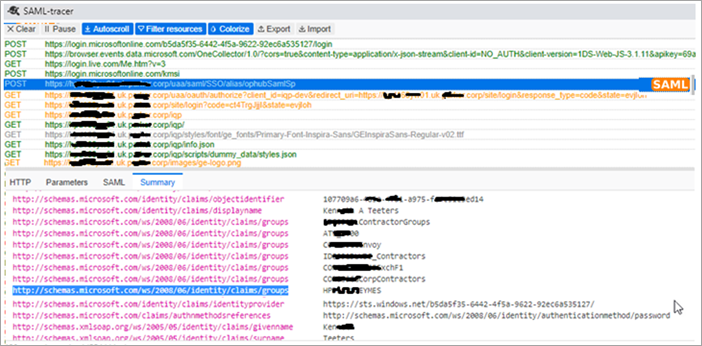
- Open SAML-tracer from your browser extensions.
- Log in to Operations Hub to reproduce the SSO login issue.
- In SAML-tracer, look for
POSTmessages, and select the Summary tab.In the following screenshot, incorrect SAML group attribute names were detected, and replaced with the correct ones to fix the login issue.