Autologin Configuration Checklist
CIMPLICITY supports Windows Autologin functionality to connect to Proficy Authentication server in a domain-based environment. You can use this topic as a checklist to know how Autologin feature in CIMPLICITY works. For more detailed information on Proficy Authentication, it is recommended that you read the Proficy Authentication help at https://www.ge.com/digital/documentation/uaa/version2023/index.html.
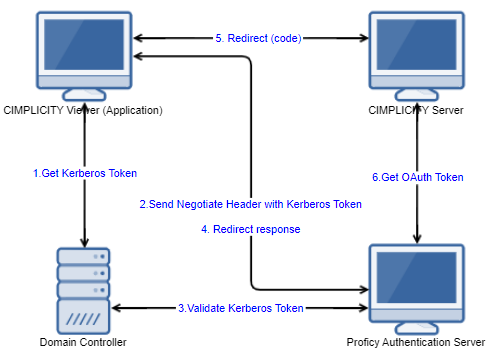
| Node | Configuration | Description |
|---|---|---|
| CIMPLICITY Nodes | Configure Security Policy |
Ensure that correct encryption types are associated to Kerberos authentication is
selected.
Encryption types allowed for Kerberos: AES256_HMAC_SHA1 Configure Proficy Authentication on CIMPLICITY server.
Note:
|
| Domain Controller | Configure Security Policy |
Ensure that correct encryption types are associated to Kerberos authentication is
selected.
|
| Create Service Principal Name |
Before you begin, ensure that you have performed the following:
To perform this task, you must be an administrator.
<FQDN>- Fully Qualified Domain Name (FQDN) of the server on which Proficy Authentication service is running. <user account>- Dedicated user account created for Proficy Authentication service. |
|
| Generate Keytab File |
Before you begin, ensure that you have performed the following:
To perform this task, you must be an administrator.
You can do the following to verify if the service principal is mapped to the
dummy account, and a keytab is created:
|
|
| Proficy Authentication Server | Configure Security Profile |
Ensure that correct encryption types are associated to Kerberos authentication is
selected.
|
| Configure Proficy Authentication Services |
Before you begin, ensure that you have performed the following:
To perform this task, you must be an administrator:
|
|
| Configure LDAP Provider |
Add an LDAP provider and make appropriate mappings. Ensure that the logged in user name can work with user filter specified in Proficy Authentication. |