Generate Keytab File
Generate the Kerberos keytab file.
- Log in to your system and open the Windows Command Prompt application.
-
Run the following command replacing with the appropriate code:
ktpass -out <filename> -princ HTTP/<service pincipal name> -mapUser <user account> -mapOp set -pass <password> -crypto AES256-SHA1 -pType KRB5_NT_PRINCIPALCode Replace With <filename>Name of the keytab file. The file is created at the default location. You also have the option to specify an absolute path for file creation. For example,
-out c:\Documents\myskullcave.keytab.<service pincipal name>Enter the service principal name that was created in the following format: HTTP/[email protected]<User account>Enter the same dummy user account that was used during creating the service principal name. For example,
ghost1.<password>Proficy Authentication dummy user account password. AES256-SHA1Encryption algorithm you want to use. KRB5_NT_PRINCIPALEncryption type you want to use. If the keytab is successfully created, the log should look something like this:C:\Users\Administrator>ktpass -out c:\Temp\SACHINJOHUB21VM.uaatestad.ge.com.keytab -princ HTTP/[email protected] -mapUser Mark -mapOp set -pass Gei321itc -crypto AES256-SHA1 -pType KRB5_NT_PRINCIPAL Targeting domain controller: uaatestad.uaatestad.ge.com Using legacy password setting method Successfully mapped HTTP/SACHINJOHUB21VM.uaatestad.ge.com to Mark. Key created. Output keytab to c:\Temp\SACHINJOHUB21VM.uaatestad.ge.com.keytab: Keytab version: 0x502 keysize 105 HTTP/[email protected] ptype 1 (KRB5_NT_PRINCIPAL) vno 3 etype 0x12 (AES256-SHA1) keylength 32 (0x3fb2a2824864a6b3617bfa4a6458af83534efdb8a3eac08b02316cce9c4ee7fc)Example of a failed log:C:\Windows\system32>ktpass -out c:\Temp\win16-sachin.uaatestad.ge.com.keytab -princ HTTP/[email protected] -mapUser John -mapOp set -pass Gei321itc -crypto AES256-SHA1 -pType KRB5_NT_PRINCIPAL Targeting domain controller: uaatestad.uaatestad.ge.com Using legacy password setting method Failed to set property 'userPrincipalName' to 'HTTP/[email protected]' on Dn 'CN=John,CN=Users,DC=uaatestad,DC=ge,DC=com': 0x13. WARNING: Failed to set UPN HTTP/[email protected] on CN=John,CN=Users,DC=uaatestad,DC=ge,DC=com. kinits to 'HTTP/[email protected]' will fail. Successfully mapped HTTP/win16-sachin.uaatestad.ge.com to John. Key created. Output keytab to c:\Temp\win16-sachin.uaatestad.ge.com.keytab: Keytab version: 0x502 keysize 102 HTTP/[email protected] ptype 1 (KRB5_NT_PRINCIPAL) vno 9 etype 0x12 (AES256-SHA1) keylength 32 (0x8b551a22050935e9ace848cacbacc86a4eb845e63b6461d4f31b7d815158cf6c)
- Go to .
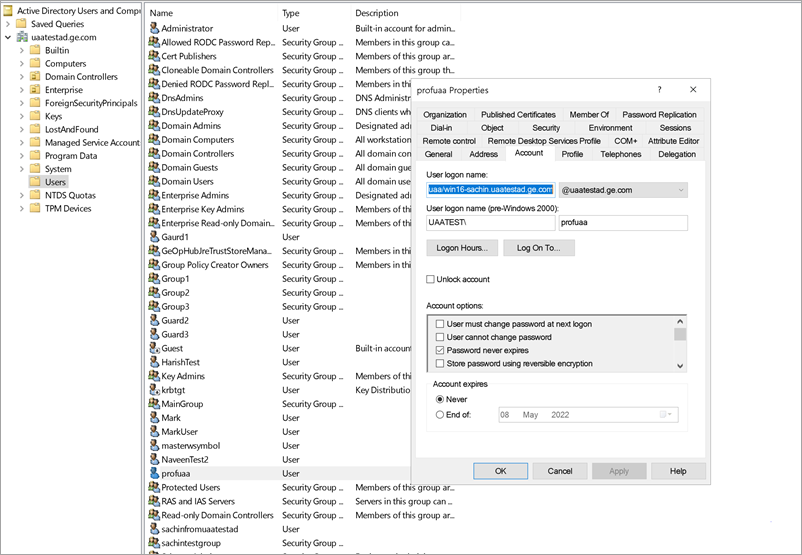
- Access the properties of the user account for which you created the keytab file.
- On the Account tab, verify User logon name. is pointing to your service principal name.
- Copy the keytab file on the machine, where Proficy Authentication is installed.
- Update the Proficy Authentication .yml file.