OIDC Federated Authentication
OIDC Federated Authentication
OpenID Connect (OIDC) is a simple identity layer built on top of the OAuth 2.0 protocol. It enables clients to verify the identity of an end-user based on the authentication performed by an authorization server or identity provider (IdP) and obtains basic profile information of an end-user in an interoperable REST-like manner.
OpenID Connect allows one or more relying parties (RP) or clients to delegate user authentication to an OpenID Provider (OP) or authentication servers. The OpenID Provider authenticates users and provides claims to relying parties. These claims are user attributes such as first and last name, email address, and department. As a result, relying parties are freed from the need to run a login process, and users have fewer credentials to manage.
OIDC implements authentication as an extension of OAuth 2.0 protocol, it provides information about the end-user in the form of id_tokens. The id_token is a signed data structure that contains authenticated user attributes that are encoded as a JSON Web Token (JWT). In addition to identifying the end-user, or subject, the id_token also identifies the token issuer and client application to which the token was issued.
- Simple to integrate with applications.
- Works harmoniously with a wide variety of applications
- Offers features and security options that meet enterprise requirements.
- Uses JWTs for portability and support for a range of signature and encryption algorithms
OIDC Implementation in UAA
OIDC implementation in UAA facilitates the users by reducing the number of passwords and other credentials that they have to manage during the authentication process. You can configure UAA as an Open ID Identity Provider or Identity Provider to authenticate with another instance of UAA.
The following diagram shows the OIDC flow in UAA.
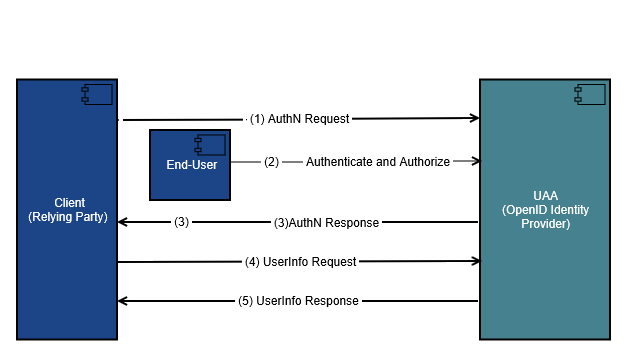
- The Client (Relying Party) sends a request to the UAA or any configured External OpenID Identity Provider.Note: In the above flow, we have shown UAA as the OpenID Identity Provider, you can also configure other external identity providers such as Google or your Company SSO.
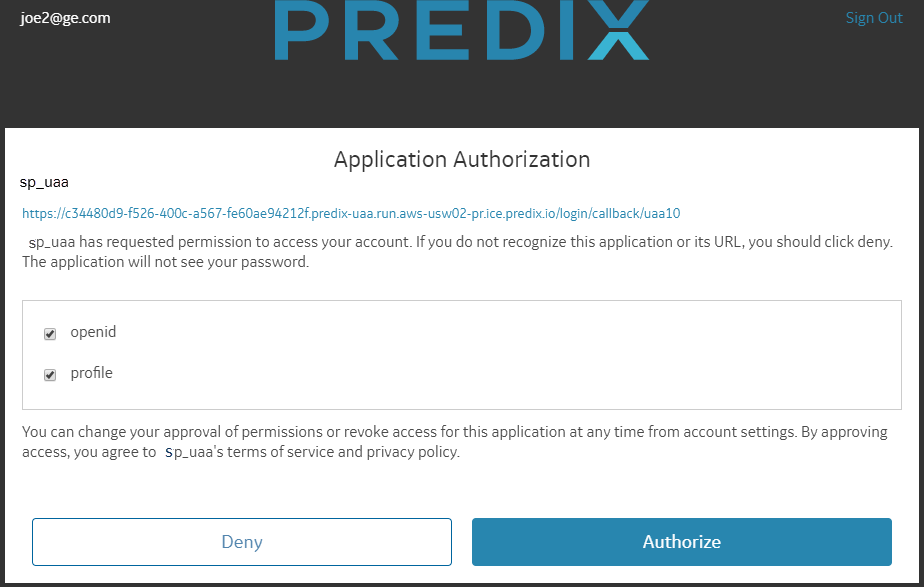
- The UAA authenticates the end-user and obtains authorization. User logs in using a web browsers and enters login credentials for authentication.
- UAA returns an ID Token and an Access Token. The AuthN response is a redirect to the client application (if configured).
- The client sends a request with the Access Token to the user info endpoint in UAA.
- UAA returns claims (data) about the end-user.
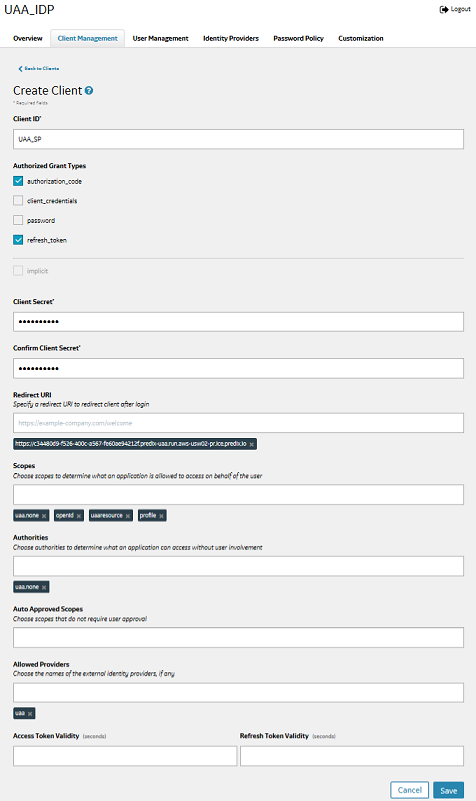
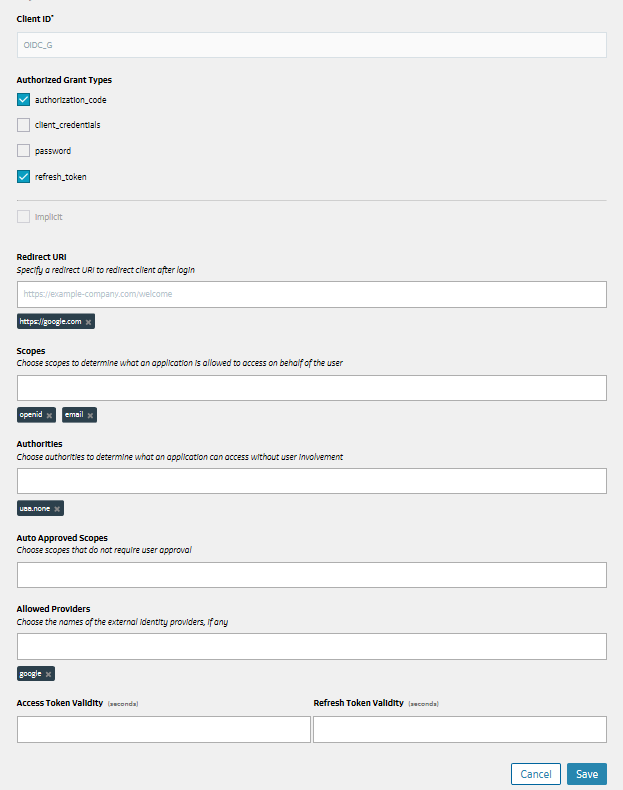
Relying Party (Client Information)
The relying party or the client is usually your web or mobile application. You must secure the following Client information for OIDC configuration.
| Fields | Values |
|---|---|
| Client ID | oidc_client_idOAuth 2.0 Client Identifier valid at the Authorization Server (OpendID Providers). |
| Client Secret | oidc_client_secretOAuth 2.0 Client Identifier secret. |
| Authorized Grant Types | authorization_codeWhen you use the authorization code grant type, the client directs the resource owner to UAA, which in turn directs the resource owner back to the client with the authorization code. |
| Redirect URI | The URL to which a user is redirected to after logging in at the OpenID Provider. requires unauthenticated access.https://*.<Identity Provider UAA base url>/login/callback/*
|
| Scopes | Include the openid scope in your client application. |
| Authorities | Include the openid authority in your client application. |
OIDC Federated Authentication Scenarios Supported in UAA
- UAA to UAA OIDC Federated Authentication
- UAA to Company SSO Authentication
- UAA to Trusted External Identity Provider Authentication
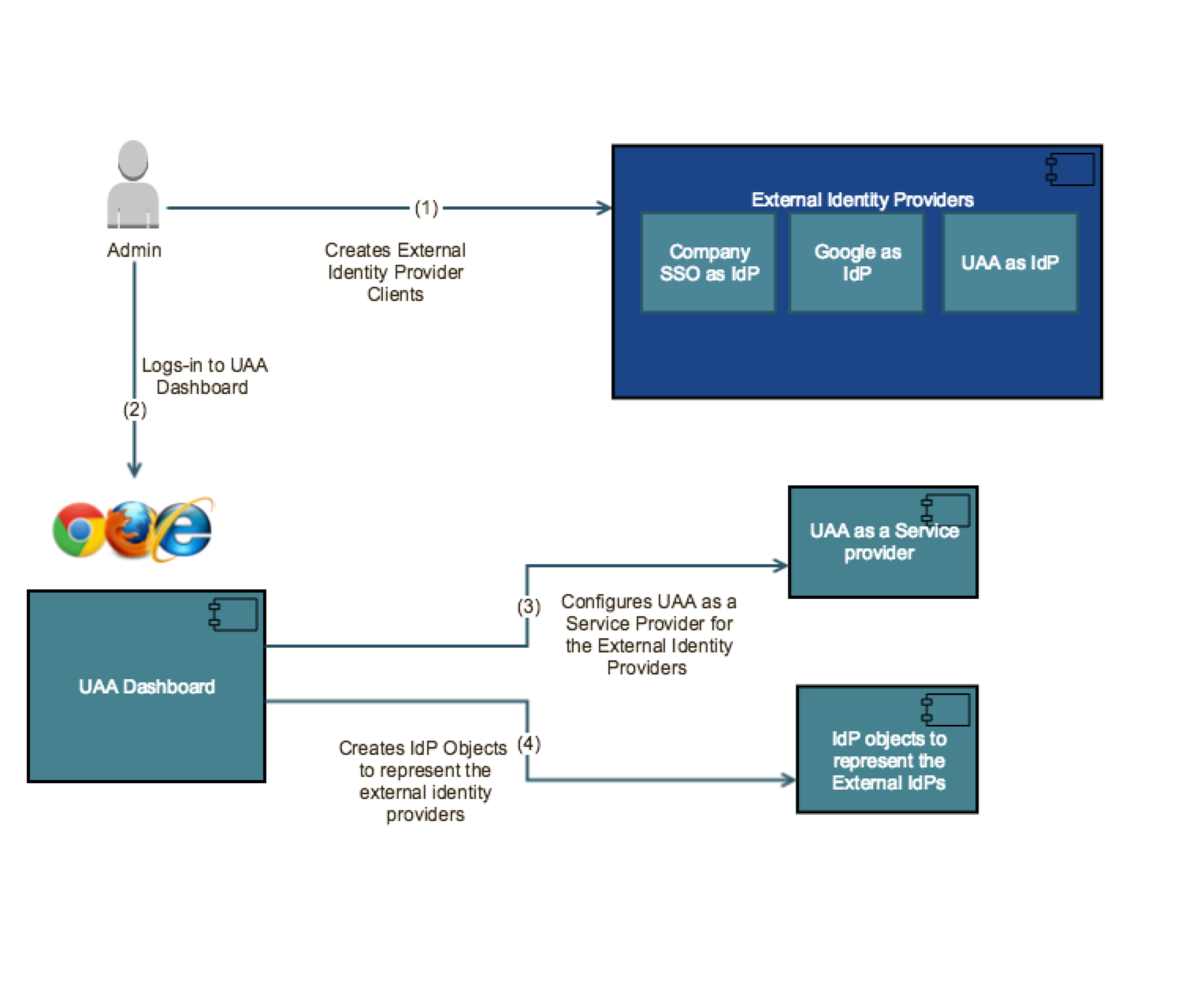
- Creates external identity provider clients for OIDC federated authentication.
- Logs-in to the UAA dashboard.
- Creates UAA service provider for external identity providers.
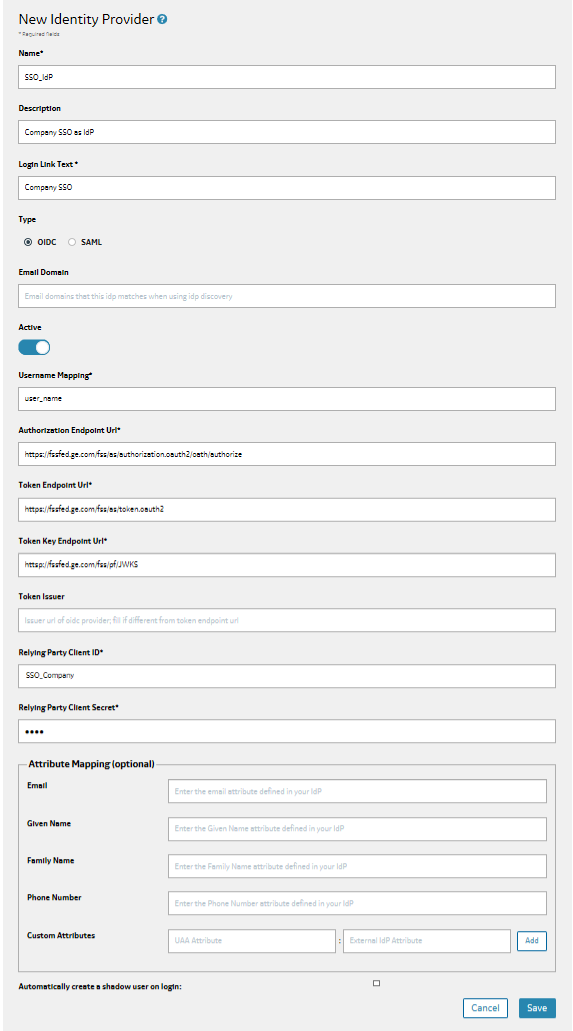
- Creates IdP objects to represent the external identity providers.
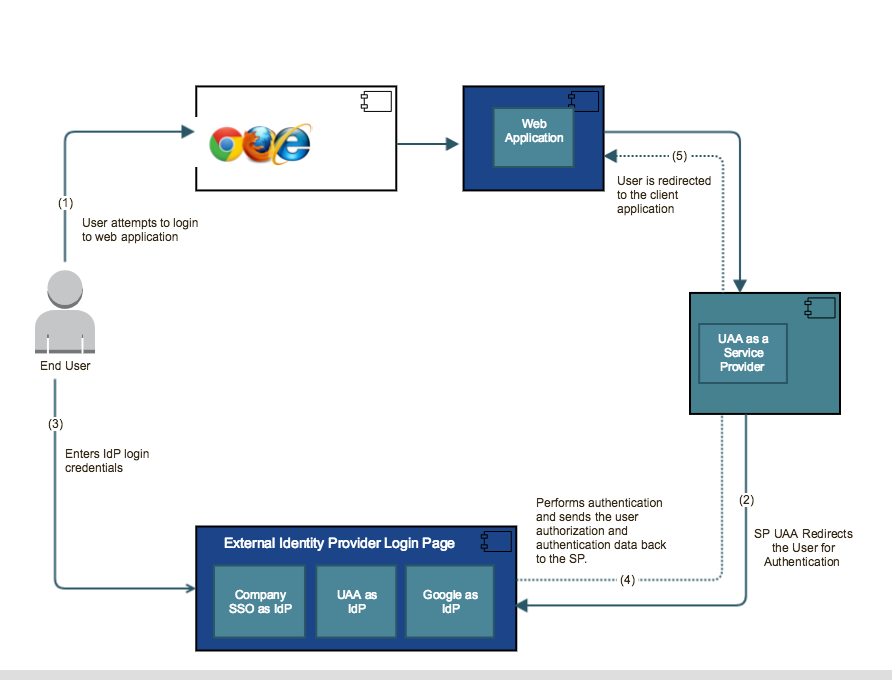
- User attempts to login to the web application and is directed to UAA service provider.
- UAA service provider redirects the user to external identity providers for authentication.
- User logs in to the External identity and enter the IdP login credentials. The external identity providers perform authentication and sends the user authorization and authentication data back to the UAA service provider. UAA generates access and id tokens based on user authentication.
- User is redirected to the client application after the authentication is completed.
UAA to UAA OIDC Federated Authentication – You can configure OIDC federated authentication between two instances of UAA, and designate one as the identity provider (IdP) and the other as the service provider (SP) to allow the UAA service provider users to redirect to UAA identity provider for authentication. UAA (SP) instance acts as the server that receives the authentication and authorization data while the UAA (IdP) acts as the server that receives the authentication request, performs user authentication, and sends the authentication and authorization data back to the SP. See uaas-oidc-federated-authentication.html#task_qw1_d1s_ycb for details on configuring UAA as a Service Provider.
openidand any other scopes specific to your Company's SSO configuration that when UAA exchanges the authorization code for Company SSO token, the token includes required attributes for user authentication. You must set up your Company SSO as the allowed provider for your IdP client. See uaas-oidc-federated-authentication.html#task_hyh_qcq_vcbUAA to Trusted External Identity Provider – You can also configure an OIDC compliant external identity provider such as Google to perform user authentication with UAA as the service provider (SP) to allow the users to redirect to the external identity provider for authentication. When Google is set up as an external OIDC federated identity provider, users can log in using their Google account credentials. UAA (SP) must be set up with the required openid and email scopes so that when UAA exchanges the authorization code for Google IdP token, the token includes required attributes for user authentication. You must set up your Google IdP client before configuring UAA as the service provider for OIDC federated authentication. See uaas-oidc-federated-authentication.html#task_vss_53t_ycb
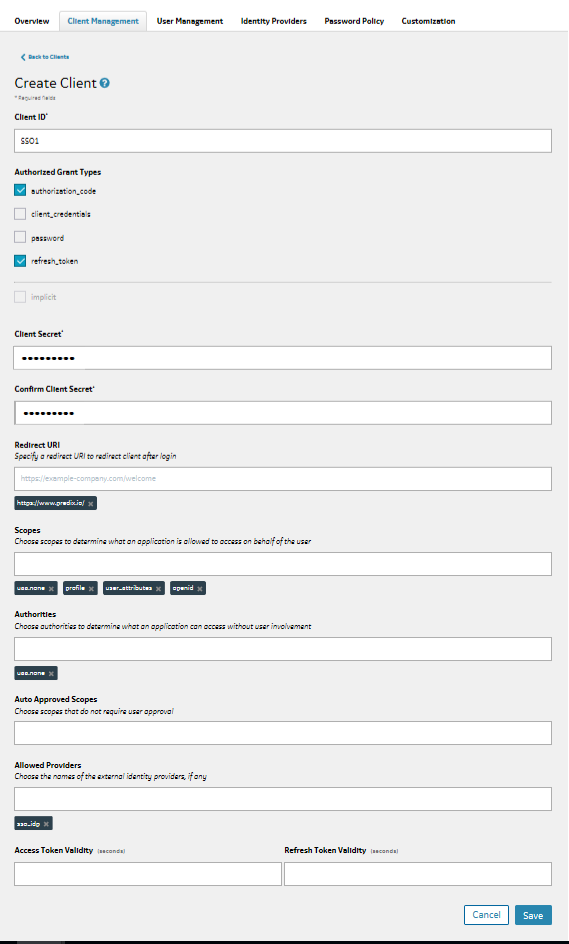
Configuring UAA as a Service Provider for OIDC Federated Authentication
About This Task
Before You Begin
- Create your external identity providers and secure the required client information for authentication. If you are configuring OIDC federated authentication between two instances of UAA, see uaas-oidc-federated-authentication.html#task_gw4_5hc_4cb.
- Log In to Predix.io and go to the Console view.
- Create or select a UAA instance that you want to configure as your identity provider.
The Client Management form represents your Client application, you can use the information in the Client Management form to verify your Redirect URIs or other client specific information.
Procedure
Example
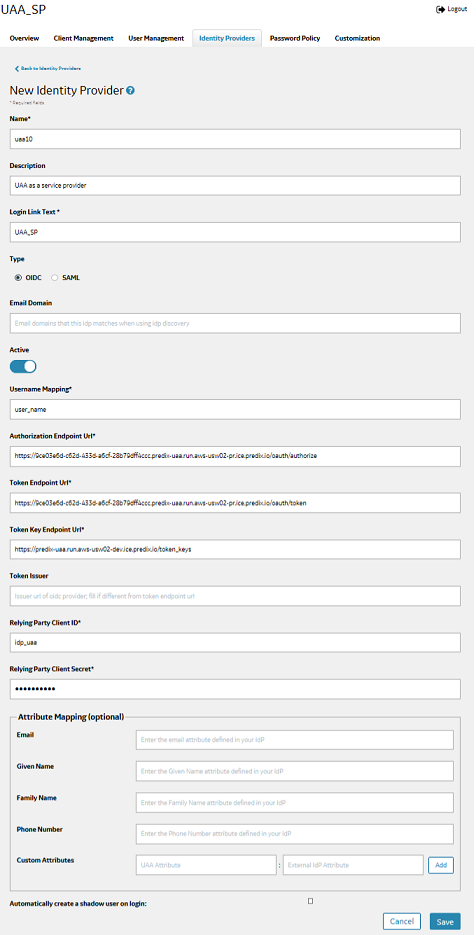
What To Do Next
Configuring UAA as an OIDC Identity Provider
About This Task
Before You Begin
- Select or create a UAA instance that you want to set up as your IdP.
Procedure
What To Do Next
Verifying UAA to UAA OIDC Configuration
Before You Begin
- Redirect URI for the UAA(IdP)
- User credentials (username, email, and password) for the user that you created with OpenId scope in UAA(IdP). See Configuring UAA to UAA OIDC Federated Authentication
Procedure
Example: Configuring UAA SP for OIDC Authentication Using Company SSO IdP
About This Task
Before You Begin
- Create the Company SSO identity provider information.
- Create or select a UAA instance that you want to configure as the SP for your Company SSO IdP.
Complete the following procedure to configure Company SSO as the external identity provider.
Procedure
Example: Verifying Company SSO as an OIDC IdP Configuration
Before You Begin
Ensure that you have your UAA service provider instance link handy. Your UAA instance link must be in this format, https://<uaa_zone_id>.<uaa_url>/login.
Procedure
Example: Configuring UAA to Google IdP OIDC Federated Authentication
About This Task
Follow these steps to set up your Google IdP Client:
Setting Up Google IdP Client Information
Procedure
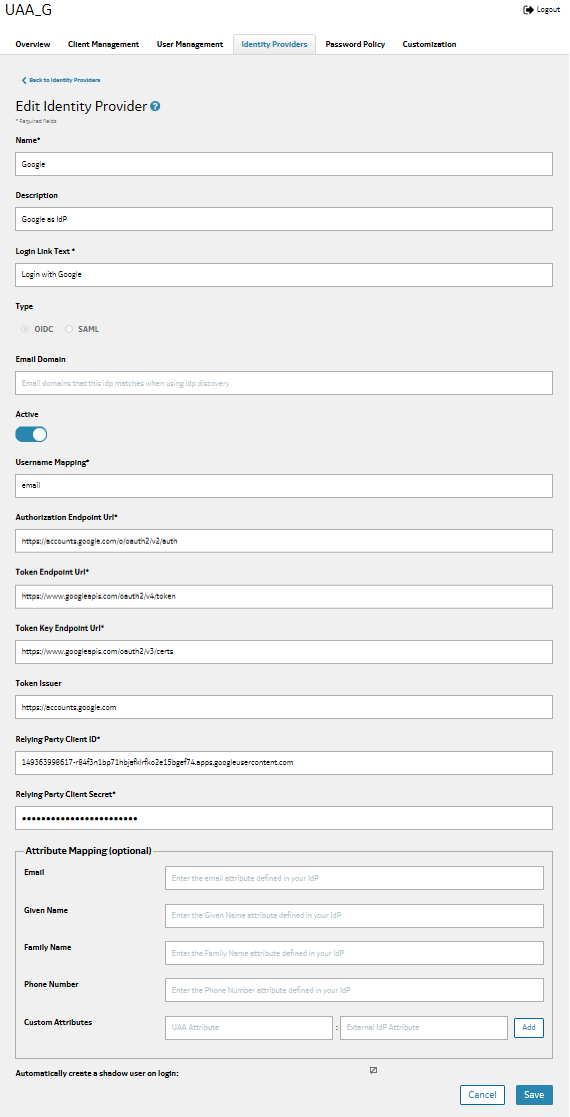
Configuring UAA as an SP for OIDC Authentication with Google IdP
About This Task
The following example shows how to configure UAA as a service provider for Google identity provider.
Before You Begin
- Configure your Google IdP client information as outlined in the Setting Up Google IdP Client Information section.
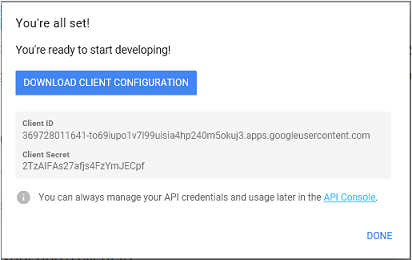
- Download and save the Client ID and Client Secret for your Google IdP client. You will need this information to configure UAA as a service provider.
Procedure
What To Do Next
Example: Updating Google IdP for Required Scope
About This Task
email scope. This feature is not available through the UAA dashboard and you must use the uaac commands through your Terminal or Command Prompt to perform this task. Follow these steps to update the IdP using the uaac to include the email scope