Multifactor Authentication
UAA Multifactor Authentication
UAA multifactor authentication (MFA) is a mechanism to add an additional factor to user authentication and verification process. The MFA works in conjuction with the primary method for user authentication i.e., using the password. When MFA is implemented, users attempt to login with their password and are redirected to MFA registration or code verification page. Users are signed in only after the second authentication factor is satisfied.
Creating an MFA Provider
About This Task
Multifactor authentication (MFA) providers are scoped to an IdentityZone in UAA. As an Admin, you can create an MFA provider on a per zone basis. Once you set up MFA for a UAA zone, you can enable or disable the MFA provider for users in that zone.
Procedure
What To Do Next
After you create an MFA provider for a UAA zone, you must enable MFA for users in that zone, see uaas-multifactor-auth.html#task_uty_j4b_xdb for more information.
Enabling an MFA Provider for a UAA Zone
About This Task
When MFA provider is enabled, all users in a given zone are required need to enter their password and go through the Google Authenticator code verification process to successfully authenticate with UAA.
Procedure
- Set the
mfaConfigproperty in the IndentityZone configuration to enable MFA for that zone. - Update the IndentityZone configuration using the update the IdentityZone API. The
providerNameis the unique name of the provider used at the time of creation.
Disabling an MFA Provider for a UAA Zone
About This Task
Procedure
mfaConfig property to false to disable the MFA for a given zone. Understanding MFA User Flow
If you are a first time application user, you must register your phone application with your UAA account before you start using the Google Authenticator.
Registering First Time Application Users
About This Task
You can start using the Gooogle Authenticator after you register your phone application with your UAA account.
Procedure
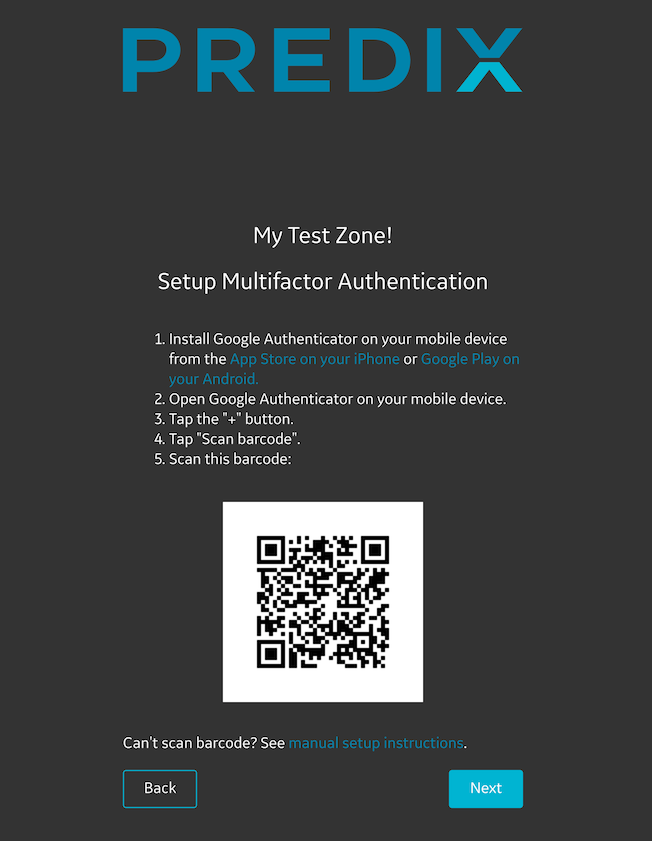
What To Do Next
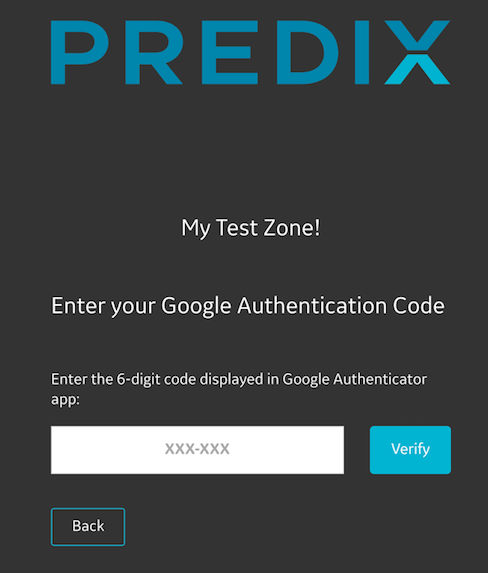
Entering One-Time Authentication Code
After you register your applicationw ith UAA account, you can use the generated 6-digit Google Authentication code to complete the second factor of the authentication process.
Procedure
Deleting MFA Registration
You can delete the MFA registration for a specific user. The MFA registration for a user is tied with the Google Authenticator application used during MFA configuration. If the user uninstalls the application or switches to a new phone, the UAA account must registered again with a new authenticator application.
- Admins can delete the MFA credentials for a user using delete MFA registration API. Note: Deleting an MFA provider will delete the MFA registration for all the users for that provider.
- Any users with deleted MFA registration must go through MFA Registration process as described in the uaas-multifactor-auth.html#task_lmd_pj2_wdb
.