General Reference
Requirements
For successful data transfer between ServiceMax and Predix Essentials, your installation must meet minimal requirements.
Each component listed must also meet the preferred system requirements.
- ServiceMax Version Winter '18 or later.
ServiceMax Data Model
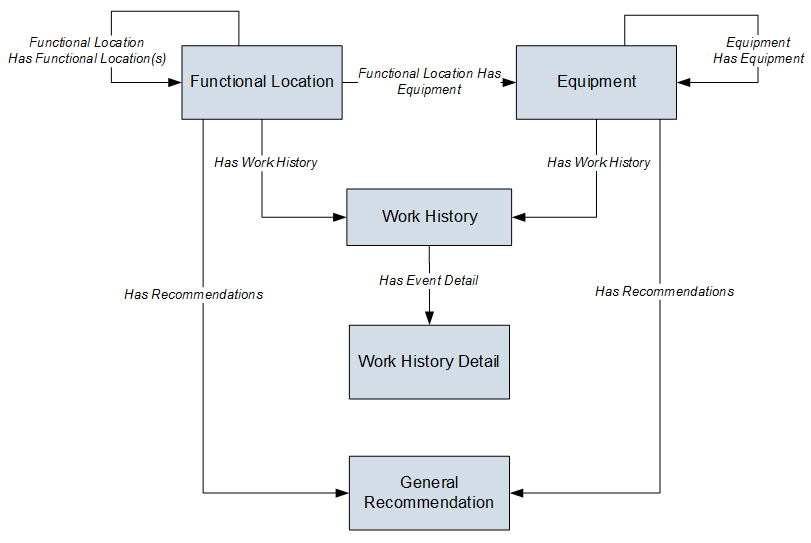
The Predix Essentials ServiceMax feature consists of entity families, relationship families, and business rules. When attempting to understand and make use of the Predix Essentials ServiceMax functionality, it can be helpful to visualize the ServiceMax data model. You can use the ServiceMax to create and view records. This documentation assumes that you are familiar with the concept of records and viewing records in the Predix Essentials Record Manager.
About Interface Log Records used by the Service Request and Work Order Interface Record
Each time an interface is run, an Interface Log record is created automatically to store information about the process, such as the status of the process (for example, Completed with warnings), the date the interface was run, and the parameters that were used to run the interface.
If the value in an Interface Log record is Completed with Warnings or Completed with Errors, a Super User or a member of the MI CMMS Interfaces Administrator Security Group can review the warnings or errors, and then change the status to Completed with Warnings (Cleared) or Completed with Errors (Cleared).
EAM System
EAM System records are used to store information about your systems to facilitate data extractions and loads.
When you transfer data from Predix Essentials to your EAM or service management system, the Predix Essentials system uses EAM System records to determine which EAM system to use.
In addition, EAM System records are used by the Equipment Adapter and the Functional Location Adapter.
This topic provides an alphabetical list and description of the fields that exist for the EAM System family. The information in the table reflects the baseline state and behavior of these fields.
This family is not enabled for site filtering, which means that records in this family can be accessed by any user with the appropriate license and family privileges. For more information, refer to the Sites section of the documentation.
| Field | Data Type | Description | Behavior and Usage |
|---|---|---|---|
| Authentication Client ID | Character | The client ID for the ServiceMax system. | Enter your unique value. |
| Authentication Client Secret | Character | The secret associated with the ServiceMax client. |
Enter your unique value. The value that you enter will be encrypted and displayed as asterisks on the datasheet. |
| Authentication Token | Character | The token assigned to the ServiceMax client. |
Enter your unique value. The value that you enter will be encrypted and displayed as asterisks on the datasheet. |
| Connection String | Character | The connection information for the system. | Note: The value of this field is for all systems that require a connection string, even though the template values contain the characters SAP. In new EAM System records, you need to delete all angle brackets and:
|
| Default EAM System? | Boolean | A value that indicates whether this system should be used by default when transferring data between your Predix Essentials system and your system. |
On the datasheet, you can select the check box to identify this system as the Default EAM System. The default EAM system is used when creating a notification from a General Recommendation when there is no technical object from which to obtain the EAM system for the creation of the notification. |
| Name | Character | The name of the system. | You can enter any name, but we recommend that you enter a name in the format <SYSID>-<CLIENT>, where <SYSID> is the System ID of the system and <CLIENT> is the Client number. By doing so, the value in the Name field will match the value that will be populated automatically in the System ID field. |
| Password | Character | The password to the system. | The password that you enter will be encrypted and displayed as asterisks on the datasheet. |
| Reconnect Delay | Numeric | Specifies the delay in seconds between when a communication failure is encountered when connecting and when the system should try to connect again. |
The default value is 0. Enter your unique value. |
| System ID | Character | The ID of the system. | This field is populated automatically after you test the connection to the system using the Test Connection link on the Associated Pages menu. Specifically, the System ID field is populated automatically with the name of the system, using the format <SYSID>-<CLIENT>, where <SYSID> is the System ID of the system and <CLIENT> is the Client number. |
| System Type | Character | EAM system type. | Enter the value SERVICE_MAX. |
| User ID | Character | The User ID of a user that can log in to the system. | None |
ServiceMax Security Groups
The following table lists the baseline Security Groups available for users within this module, as well as the baseline Roles to which those Security Groups are assigned. Roles are assigned to Security Users through permission sets.
| Security Group | Roles |
|---|---|
| MI CMMS Interface Administrator | MI Data Loader Admin |
| MI CMMS Interface User | MI Data Loader User |
The baseline family-level privileges that exist for these Security Groups are summarized in the following table.
| Family | MI CMMS Interface Administrator | MI CMMS Interface User |
|---|---|---|
| Entity Families | ||
| CMMS Interface | View, Update, Insert, Delete | View |
| CMMS Mapping | View, Update, Insert, Delete | View |
| CMMS System | View, Update, Insert, Delete | View |
| Equipment | View, Update, Insert, Delete | View |
| Functional Location | View, Update, Insert, Delete | View |
| Interface Log | View, Update, Insert, Delete | View |
| Site Reference | View | View |
| Relationship Families | ||
| Equipment Has Equipment | View, Update, Insert, Delete | View, Update, Insert |
| Functional Location Has Equipment | View, Update, Insert, Delete | View, Update, Insert |
| Functional Location Has Functional Location(s) | View, Update, Insert, Delete | View, Update, Insert |
| Has CMMS Interface | View, Update, Insert, Delete | View |
| Has CMMS Mapping | View, Update, Insert, Delete | View |
| Has CMMS System | View, Update, Insert, Delete | View |
| Has Event Detail | View, Update, Insert, Delete | View, Update, Insert |