A unique set of challenges
A new world for power generators
A radically changing energy landscape is bringing a unique set of challenges for power generators. The growth of renewables means changing operating models, as well as priorities, with an increased focused on generation agility and profitability pressures. A new normal for operations has emerged, one with more centralized operations centers and more remote workers, along with a rise in automation that demands a different skill set. Additionally, an evolving workforce means reshaping an approach to safety, priority, and productivity—and rethinking resourcing along the way.
So, how to survive and thrive in this new environment?

An integrated approach
We understand the need to take a holistic and integrated approach to power generation success – covering assets, operations and people, and that’s why our software solutions are created to help you:
- Operate critical equipment with confidence
- Enhance equipment reliability and O&M efficiency
- Increase operations flexibility and profitability
- Boost work effectiveness and safety
- Protect your assets with integrated cybersecurity technology
On-demand webinar
Plant Flexibility: Can you thrive in today’s energy industry?
On-demand
Available now
Power plants built 20 years ago weren't optimized to achieve the operational goals of today and financial challenges of the near-future. So, can we thrive in today’s industry with our existing plant capabilities? Join our webinar to learn about the new challenges of today, and the digital solutions that can potentially help you manage and enhance your operations in the future.
A complete solutions portfolio
From information gathered from the smallest sensors to mission-critical operator control systems to a full suite of industrial software applications for your entire fleet, GE Gas Power and GE Digital offer a range of integrated solutions that was created to be robust, flexible, and effective.
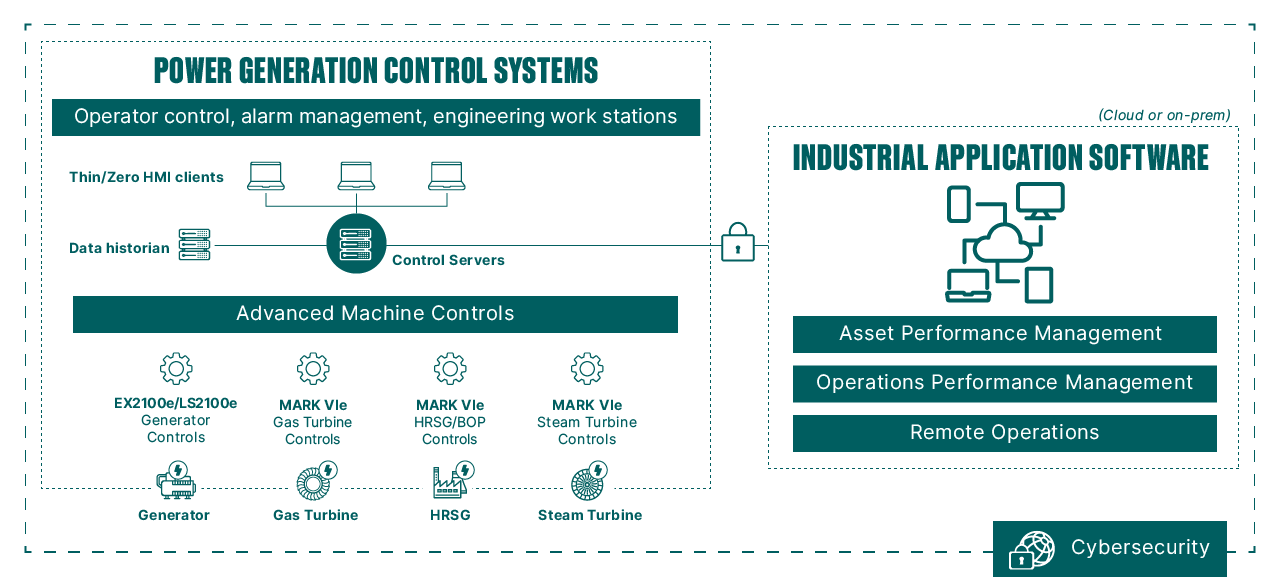
Integrated solutions
Power generation control systems
Our power generation control systems solution portfolio features tightly-integrated plant control solutions that deliver robust process control with seamless connectivity and real-time information management—to help customers enhance uptime and improve output.
Integrated solutions
Productivity application software
GE industrial application software and services help you maximize asset reliability, optimize plant efficiency and boost worker effectiveness–the keys to thriving in today’s dynamic energy market.
