Understanding Security
Your main design goal when developing a Workflow security strategy is to effectively use the Workflow security configuration.
Workflow simplifies security configuration by abstracting the three main areas that are constantly changing in a plant or facility. These main areas are:
- people/personnel
- equipment/machinery
- operational hierarchy of the people
New personnel are hired and some retire in an organization. Machinery is added, replaced, and updated. People are promoted; for example, from being an operator to a supervisor, and so on.
Workflow security accommodates all of these cases using three different constructs.
- People can be configured in groups; for example, Production Group, Maintenance Group.
- Machinery is modeled with the Equipment model using the S95 Model Editor, which defines a plant in a hierarchical fashion. An Enterprise can have multiple sites and sites can have multiple areas, and so on.
- An operational hierarchy can be defined as a set of keys that each person can hold. For example, an Operator can have keys to Start and Stop a workflow. A Supervisor can have additional keys to Create and Delete a workflow.
The first step in configuring security is to add people (users) to the system, then configure groups, and then define the key sets. Only an Administrator user can define these three fundamental pieces of security configuration. An Administrator user is created when Workflow is installed.
After the groups and key sets are defined, security can be applied to any resource in the system. For example, a group can be granted a key set on a resource such as an Enterprise in the Equipment model. Any user who belongs to the configured group will then, upon logging in to the Workflow client, have the rights granted by the key set on the Enterprise.
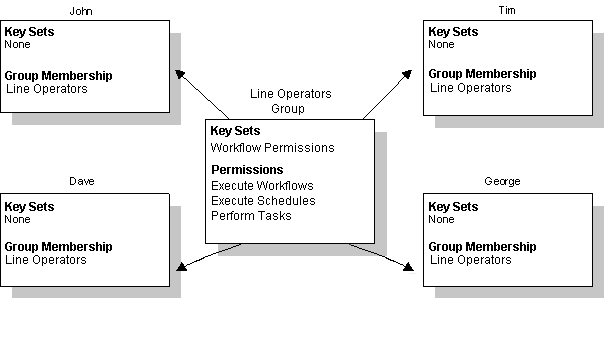
Using groups minimizes the amount of work needed to create similar users while providing you with flexibility and power. For example, when a new user comes in the plant, the user can simply be added to an existing group and will automatically inherit all the rights defined for that group.
In the following example, John, Dave, Tim, and George are all line operators. Their needs are summarized in the table.
| User Name | Key Set | Permissions |
|---|---|---|
| John | Workflow Permissions | Execute Workflows, Execute Schedules, Perform Tasks |
| Dave | Workflow Permissions | Execute Workflows, Execute Schedules, Perform Tasks |
| Tim | Workflow Permissions | Execute Workflows, Execute Schedules, Perform Tasks |
| George | Workflow Permissions | Execute Workflows, Execute Schedules, Perform Tasks |
Since each line operator requires access to the same permissions, it is possible to create a group called Line Operators that provides these privileges. After you create the group, you can assign it to each line operator, as the following figure shows.