Get Started With AppHub
AppHub Service Setup
Specific accounts and software are required before you can complete the tasks needed to set up the AppHub service.
Before You Begin
- Accounts
-
To use Predix services, you must have the following accounts.
- A Predix.io account. Go to https://www.predix.io/registration/.
When you register for a Predix.io account, an org and space is created for you in Cloud Foundry.
- A Github account. Go to https://github.com/join.
- A Predix.io account. Go to https://www.predix.io/registration/.
- Software
- The following software is required to set up the AppHub service.
| Software | Version | Description |
|---|---|---|
| Cloud Foundry CLI | Latest stable binary version | You use the Cloud Foundry CLI to deploy and manage applications and services. Download the latest stable binary from https://github.com/cloudfoundry/cli#downloads. |
| Git | Latest | Download Git from https://git-scm.com/downloads. |
About AppHub Authentication
Authentication for the AppHub service is controlled by the designated trusted issuer and is managed by the User Account and Authentication (UAA) web service, in the same manner as for other Predix platform services. You must set up a UAA service instance as the trusted issuer before you can set up the AppHub service. For more information, see About the User Account and Authentication Security Service.
Task Roadmap
Complete these tasks to set up the AppHub service.
| # | Task | Information |
|---|---|---|
| 1 | (Optional) Configure your proxy settings. | Depending on your location and network configuration, you might need to configure your proxy settings to access remote resources. See t_defining_proxy_connections_to_remote_resources.html#task_97cc6304-e168-459d-9952-a45708ff8361. |
| 2 | Create a UAA trusted issuer. | See Creating a Predix UAA Service Instance and Service Key. |
| 3 | Create an OAuth2 client. | See Creating an OAuth2 Client for AppHub. |
| 4 | Create an AppHub service instance. | See app-hub-get-started.html#task_dps_bvr_4cb. |
| 6 | Create an AppHub service key. | See app-hub-get-started.html#task_w2d_qms_4cb. |
Creating a Predix UAA Service Instance and Service Key
About This Task
You can create up to 10 instances of the UAA service in your space. If you need additional instances, you must delete an older unused instance and create a new one.
Procedure
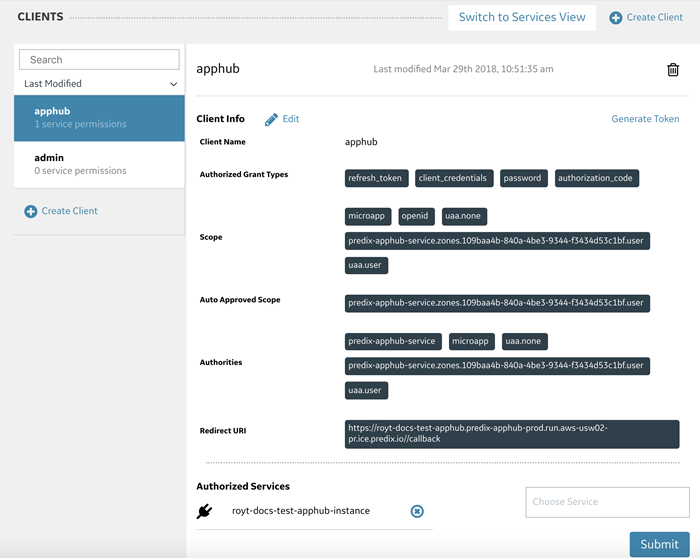
Creating an OAuth2 Client for AppHub
After you create a UAA service instance, you must create an OAuth2 client to manage user authentication and authorization for AppHub and create UAA users.
About This Task
You use the Client Management tab of the UAA Dashboard to create an OAuth2 client for AppHub, and then use the User Management tab to create users.
Procedure
Creating a Predix AppHub Service Instance
Before You Begin
To complete this task, you must first create a UUA service instance, create an OAuth2 client, and add users.
Procedure
Creating an AppHub Service Key
About This Task
You can retrieve your AppHub service instance details by creating a service key. You can then update your OAuth client with the information that you retrieve.
Procedure
What To Do Next
You can now add microapps and configuration settings to your AppHub instance. For more information, see About AppHub Microapp Configuration.